Be aware that this is done on an Always Free Account in September 2023
why this is important to know in advance: OCI is change so rapidly, it might not be working the same way a year later
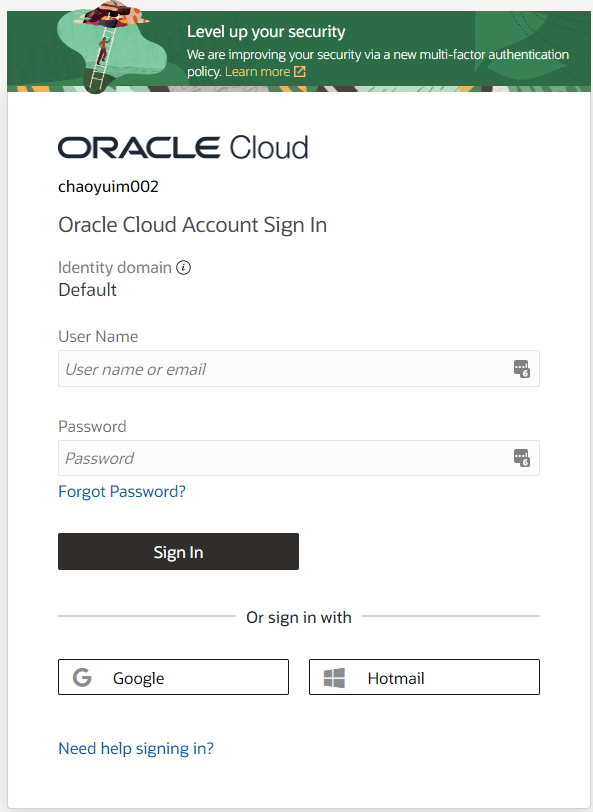
Goal: soical sign-on for both Microsoft and Google
Microsoft (azure)
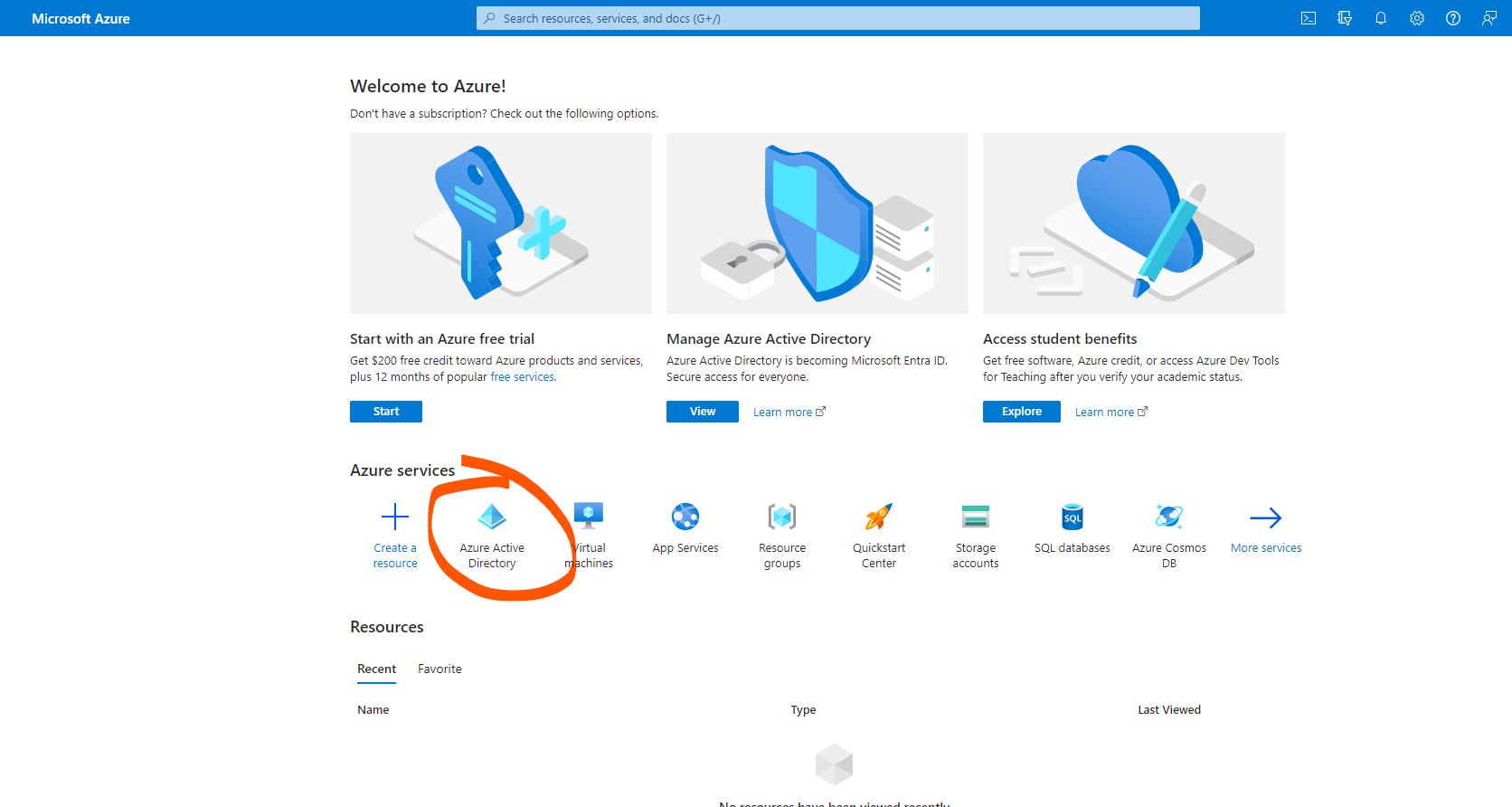
For Microsoft, we need to go to Microsoft Azure and create Azure Active Directory -> Add -> App registration
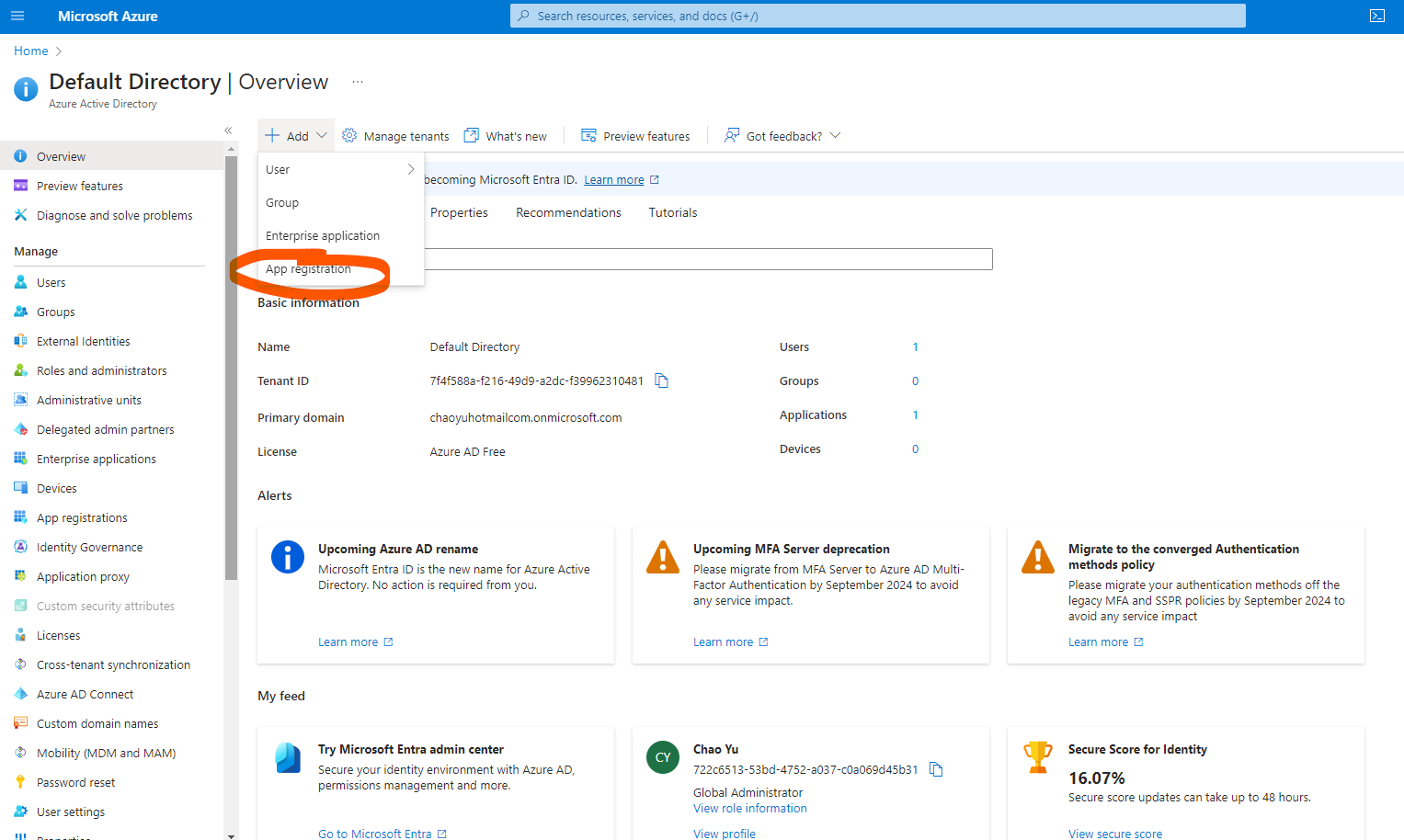
On Registration an application page, choose Personal Microsoft Accounts Only for Support Account Types, and Web for Redirect URI. Redirect URl is a must.
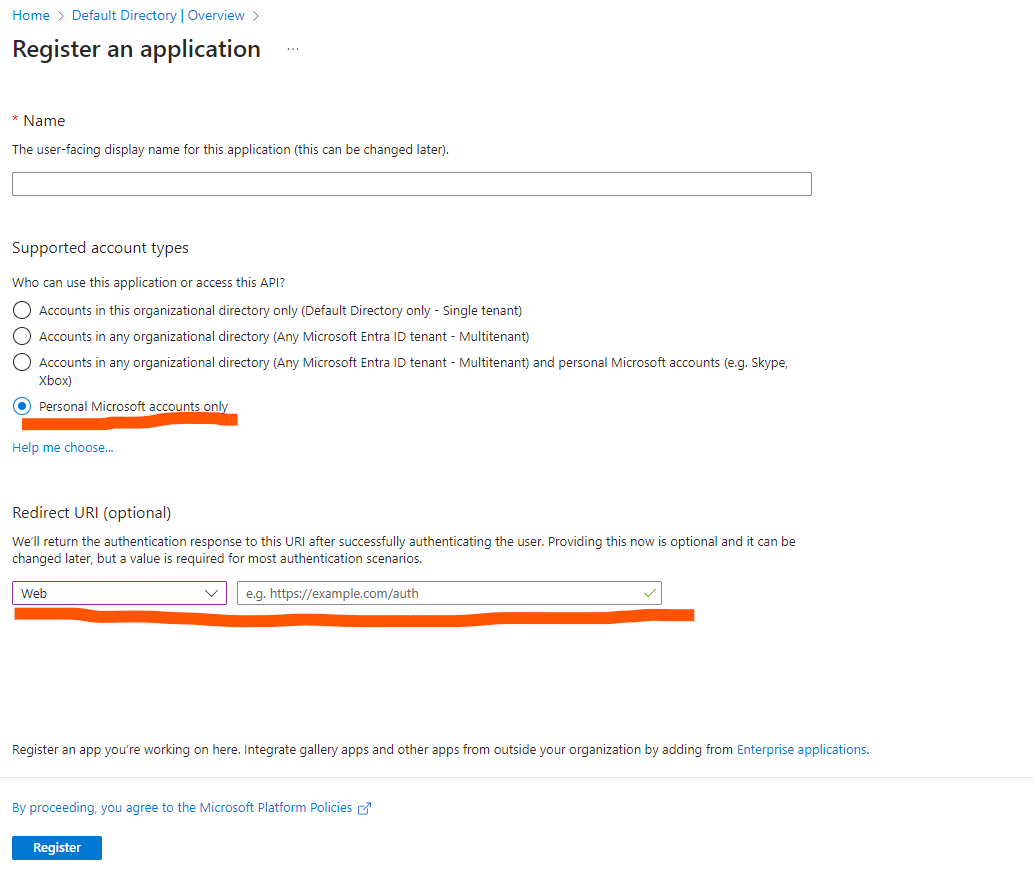
- Redirect URI for OCI are two parts
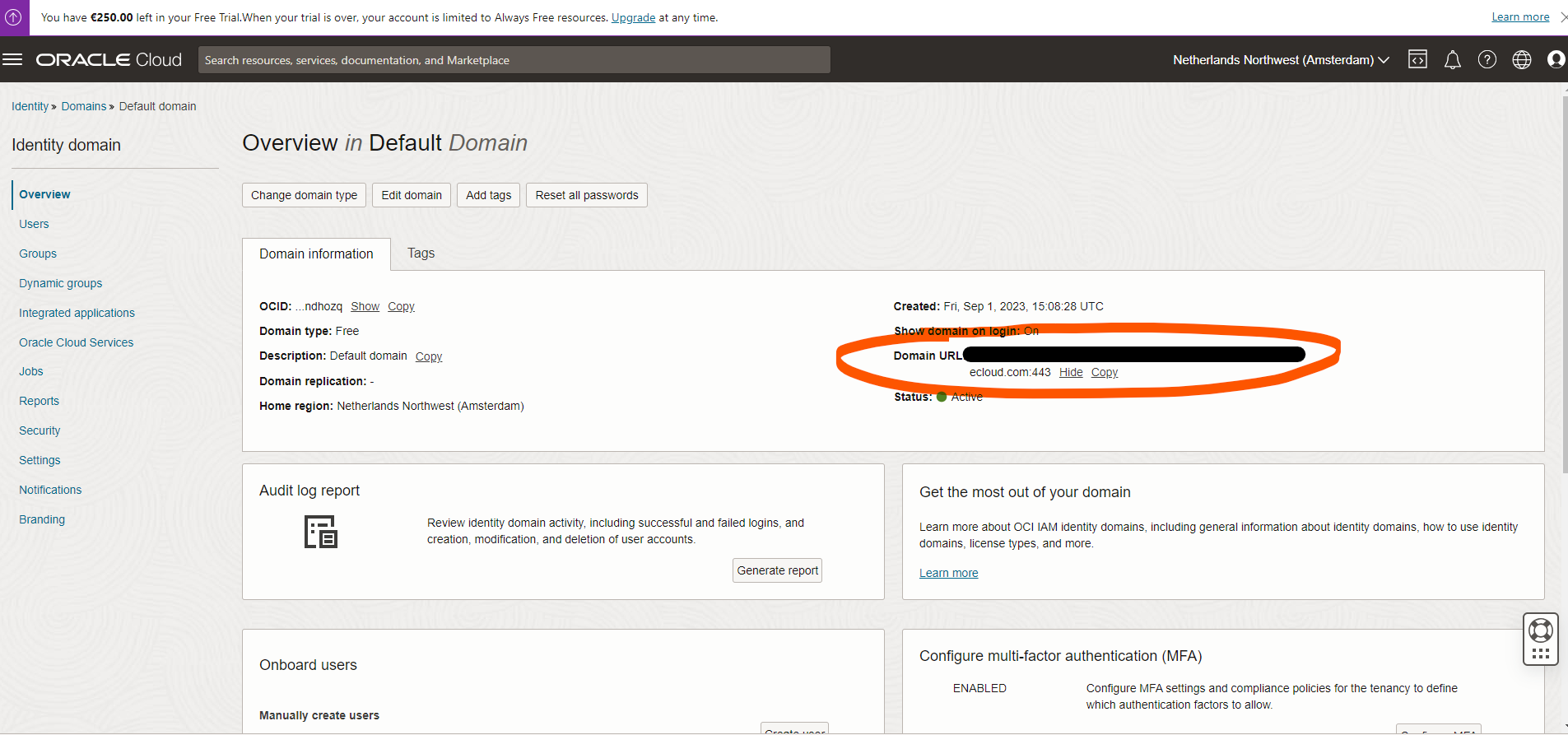
https://<Identity domain base URL>/oauth2/v1/social/callbackwe need to find thisidentity domain base url.This so called domain base url is hidden in OCI domain page Identity -> Domains -> Default Domain (or anyother domain you have) -> overview
Once Application is Registered, we need 2 things
- Client ID, client id can be found in overview -> Application (client) ID
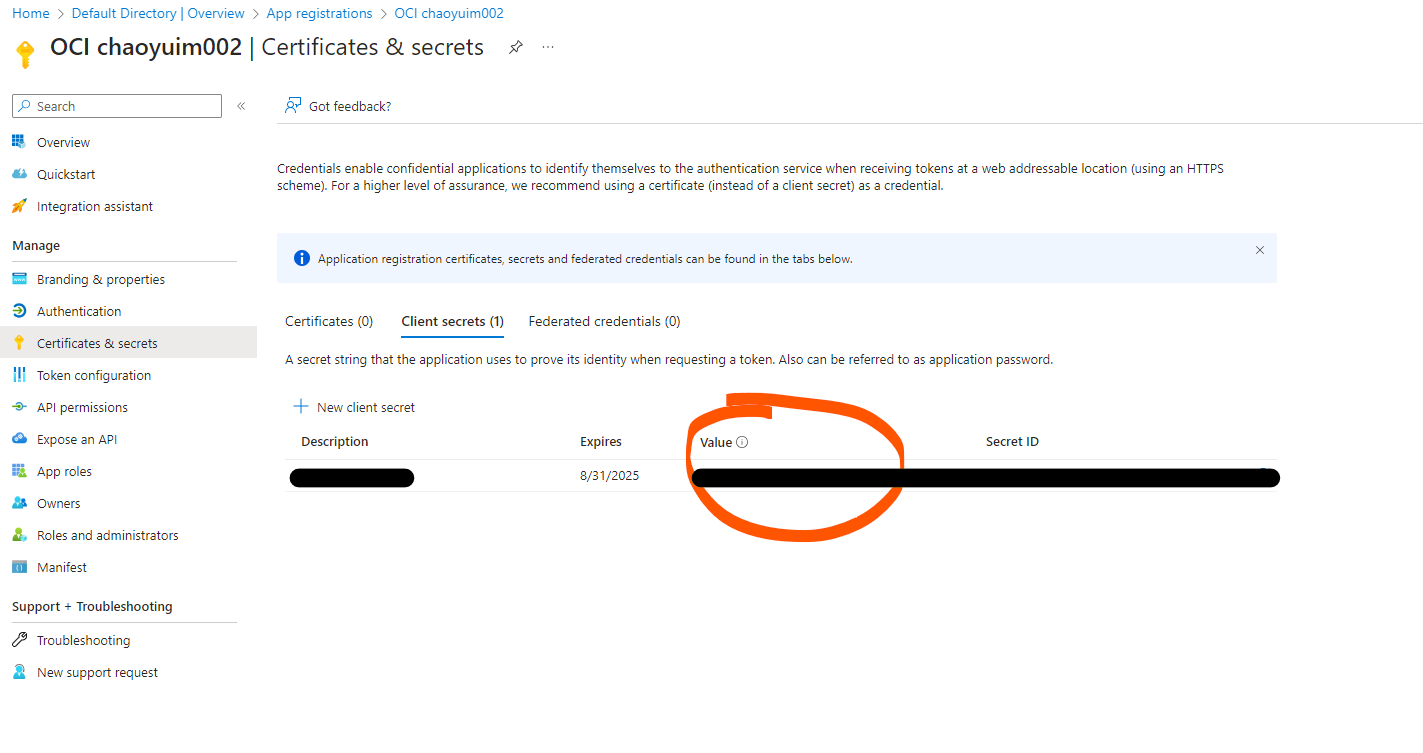
- Client Secret, client secret is created via Client Credential -> New Client Secret. Remeber to copy Value NOT secret ID

Google Console
Similar to Microsoft, we need to create a client id and secret plus redirect URL, we already know what the redirect url from the Microsoft setup, so we only need to get client id and secret.
To get them, we need to go to google console and create / or reuse an exisiting project and click on APIs & Services -> Credentials -> OAuth2.0 Client IDs
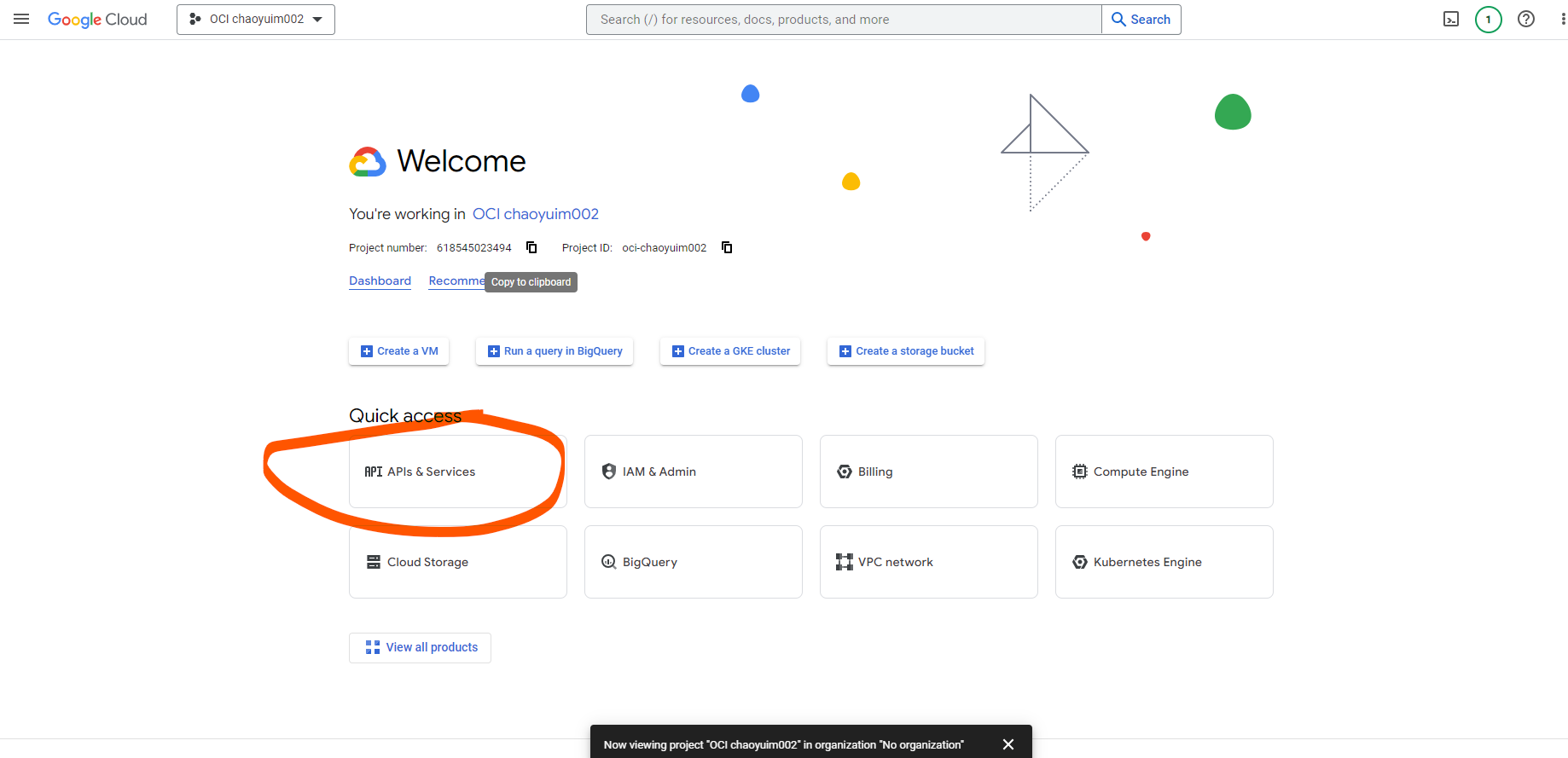
there we click on Create Credentials -> OAuth Client ID
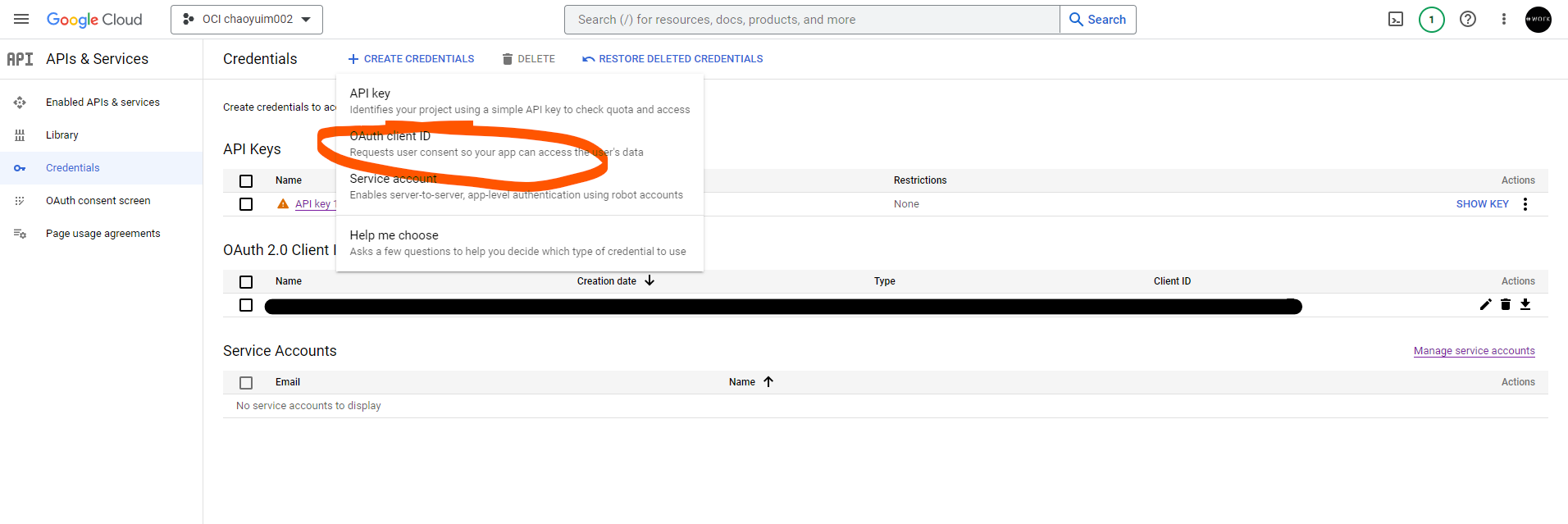
Choose Application Type Web, give it a name and most importantly Authorized Redirect URIs (this is the same redirect URL in Microsoft)
e.g https://idcs-123456.identity.oraclecloud.com/oauth2/v1/social/callback
After the creation process, we can find the client id and client secret.
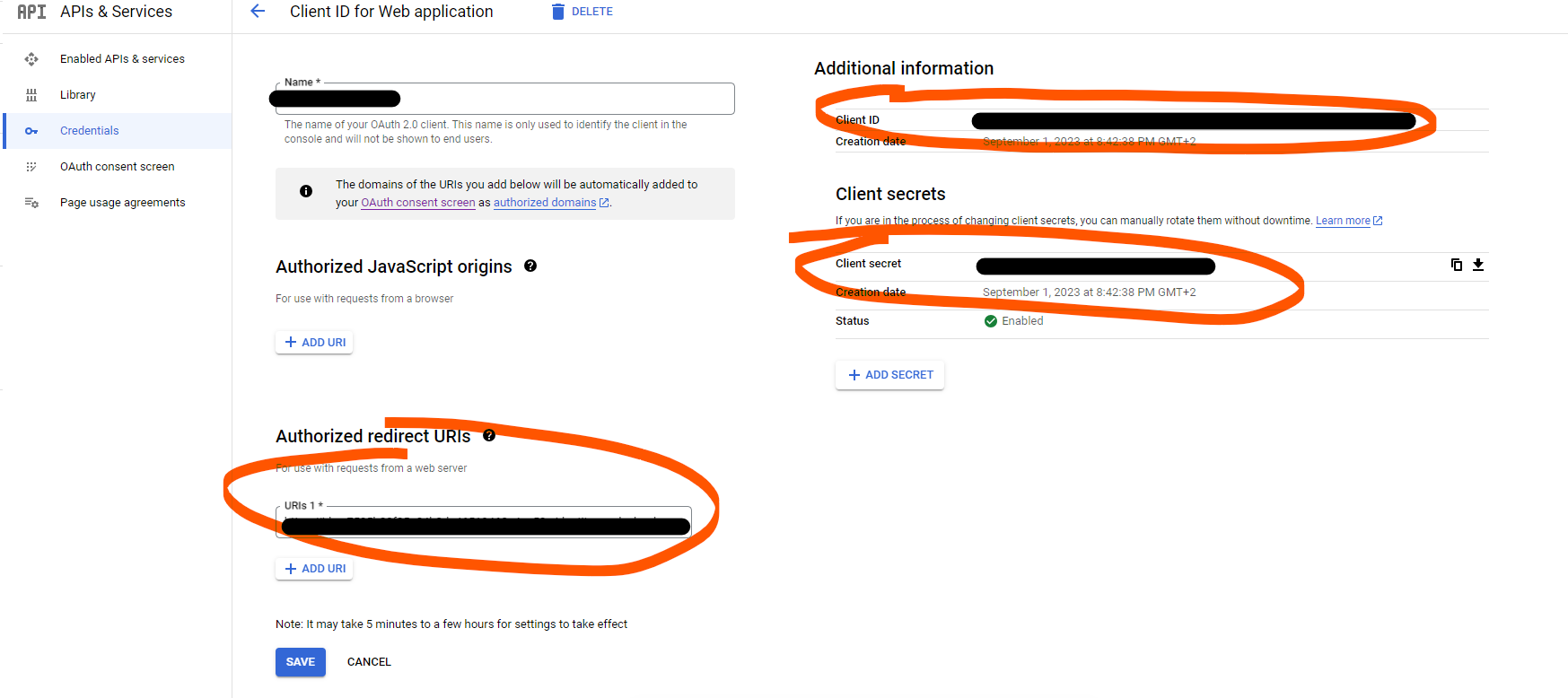
OCI
Once we have the client id and secret, it is pretty straight forward to set social sign on ( identify provider) in OCI.
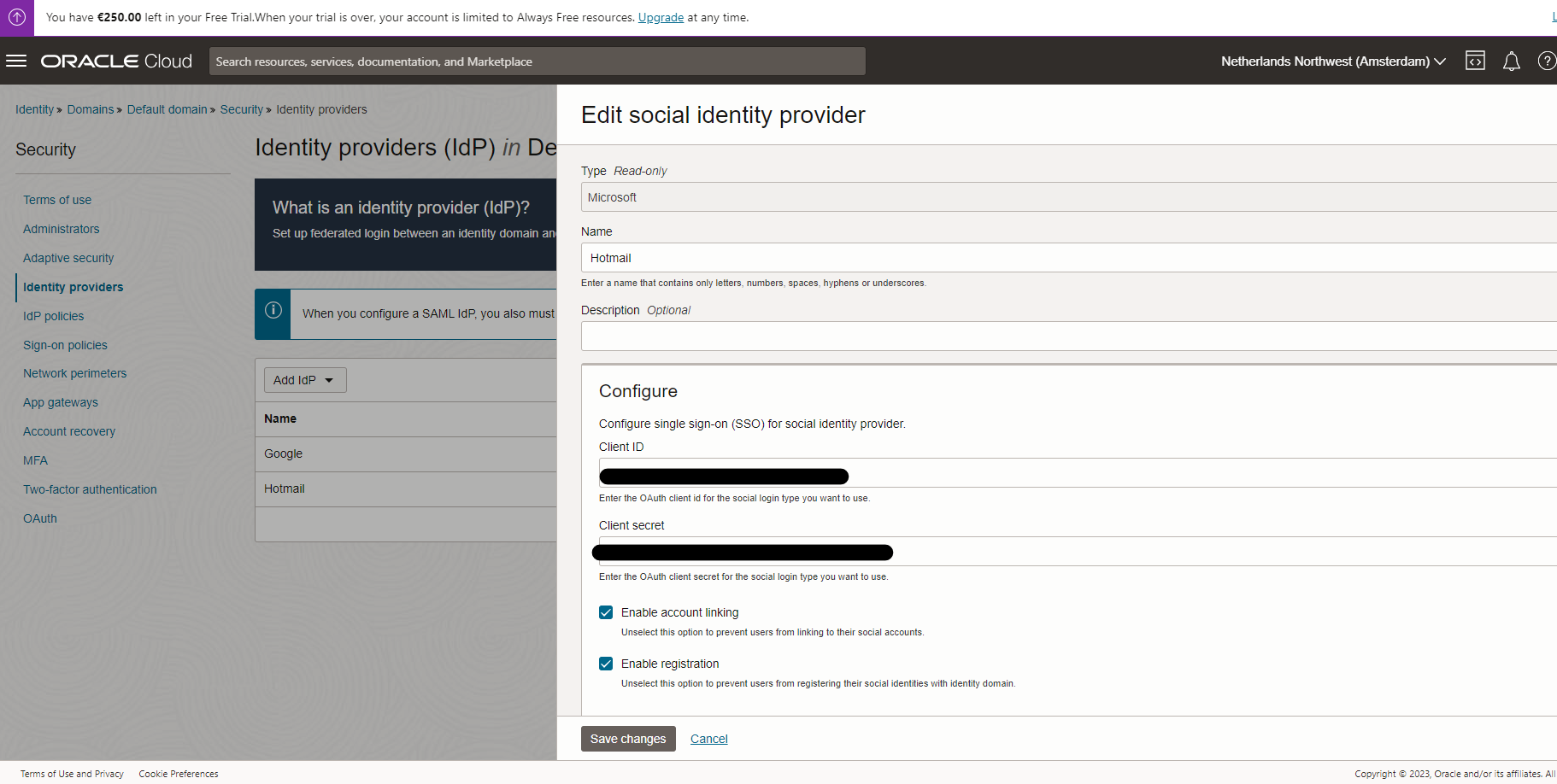
Head to Identify & Security -> Domains, click on your domain ( mine is Default). Once you are in your identify Domain click on Security -> Identity Provider and chose Add Social IdP
Choose Microsoft to set up Microsoft, here you need Client ID and Secret. For Google, it is the same. e.g
Once we have created our IdPs, we need to Active it manually.
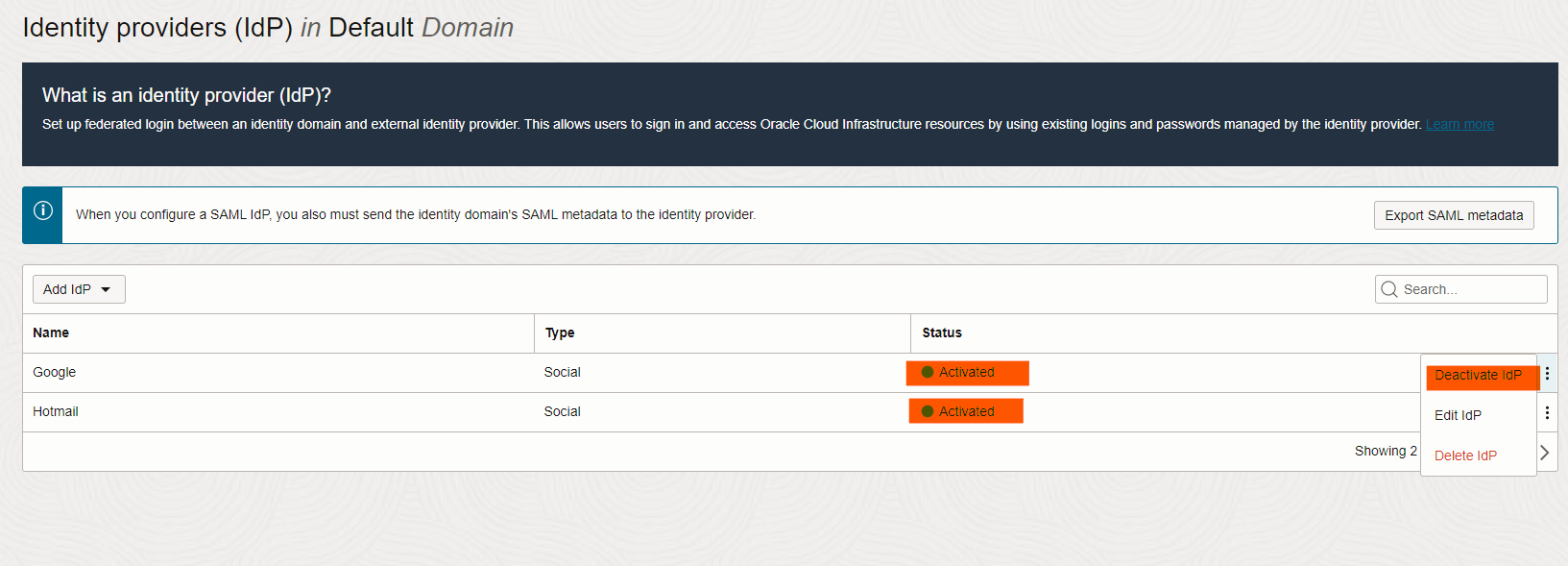
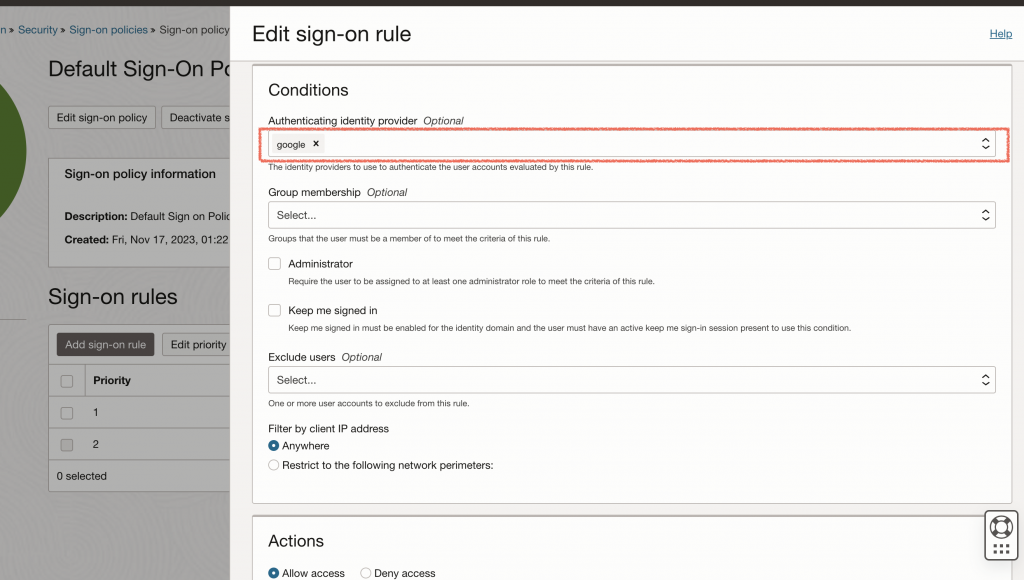
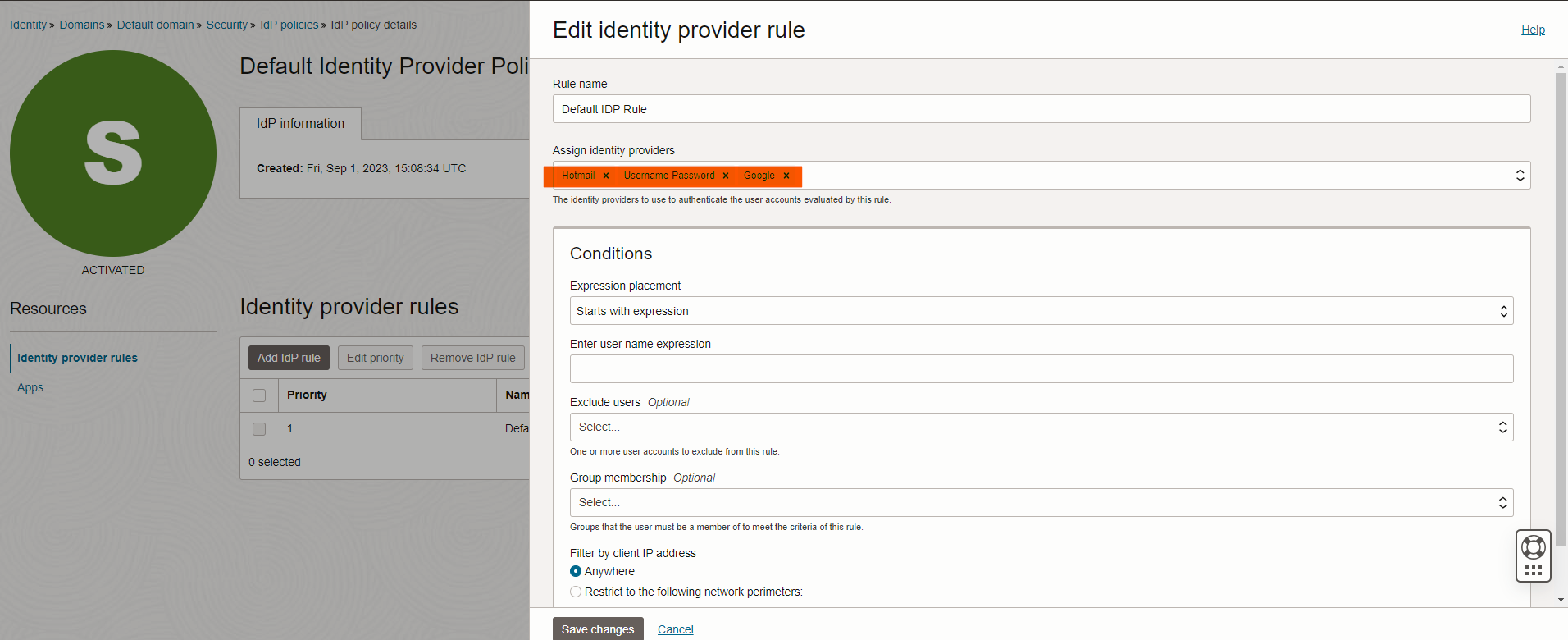
We are almost done, one last step is to add these IdPs we created to IdP policies, so the sign on will start to use it. To do it, head to IdP policies -> Default Identity Policy -> Edit first Rule and add two new identity providers and save changes
To allow email + pwd MFA and google auth at the same time
what does it mean? if you use email + pwd , user still needs TFA. if user choose google auth no need of MFA. ( ofc, it is also fine to force always MFA)
to achive this :
go to Domain > Domain ( for me it is default domain) > Security > Sign On Policy > Default Policy ( for me) > sign on Rules > create a new Rule
after Rule created, make sure it is priority 1